Before Windows Server 2008, passwords were only managed via the Default Domain Policy GPO. So only one password policy was possible without do-it-yourself. With Windows Server 2008, Microsoft introduces Password Settings Object (PSO) that enables to apply Fine-Grained password policy linked to users or groups object. However in Windows Server 2008, PSO could only be created with PowerShell command. In Windows Server 2012, Microsoft introduces a new GUI to manage Active Directory called ADAC (Active Directory Administrative Center). ADAC enables to create PSO with graphical interface.
Password Settings Object
A Password Settings Object (PSO) is an Active Directory object. This object contains all password settings that you can find in the Default Domain Policy GPO (password history, complexity, length etc.). A PSO can be applied to users or groups. When PSO is applied on some users, there are no longer using password policy from Default Policy Settings GPO. Instead they use the PSO settings.
Because PSO can be applied to a group, a user can be linked to two PSO. However only one PSO can be applied to users. So in this case an RSoP (Resultant Set of Policy) must be calculated to apply one PSO. The RSoP calculation is based on a PSO parameter called Precedence which is a number. The PSO with the lowest number win and is applied. So the lowest Precedence number is always applied.
By default only domain administrators can create and read PSO because only these accounts can create and write object in the Password Settings Container. However only write delegation on users and groups enables to apply PSO.
Deploy Fine-Grained Password Policy
Mock-up Presentation
I have created three users in my Active Directory:
- Glen Moray that belongs no group;
- John Jameson that belongs PSO-Standard Users group;
- Jack Daniel that belongs to PSO-Standard-Users and PSO-PasswordOfTheDeath groups.
Password Settings Object creation
First open ADAC from Server Manager and Tools menu.
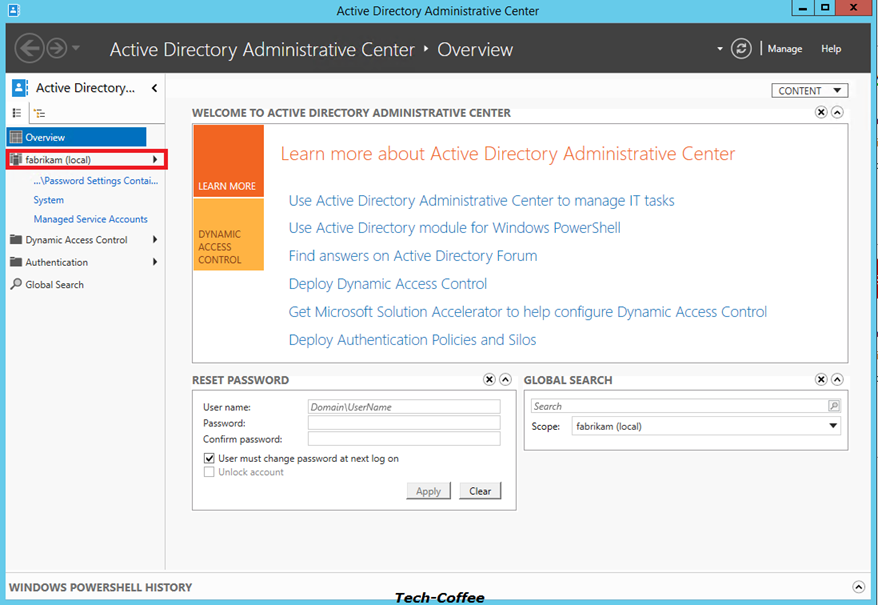
Click on your Domain (mine is called Fabrikam.com) to list containers in your domain. Click on System Container.
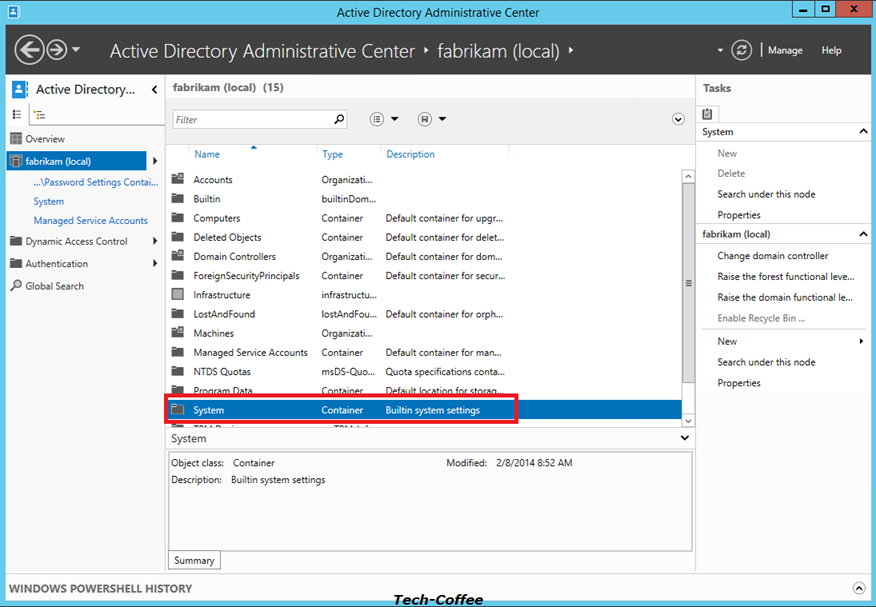
In System container, you should have the Password Settings Container. Click on it and select New on the right.
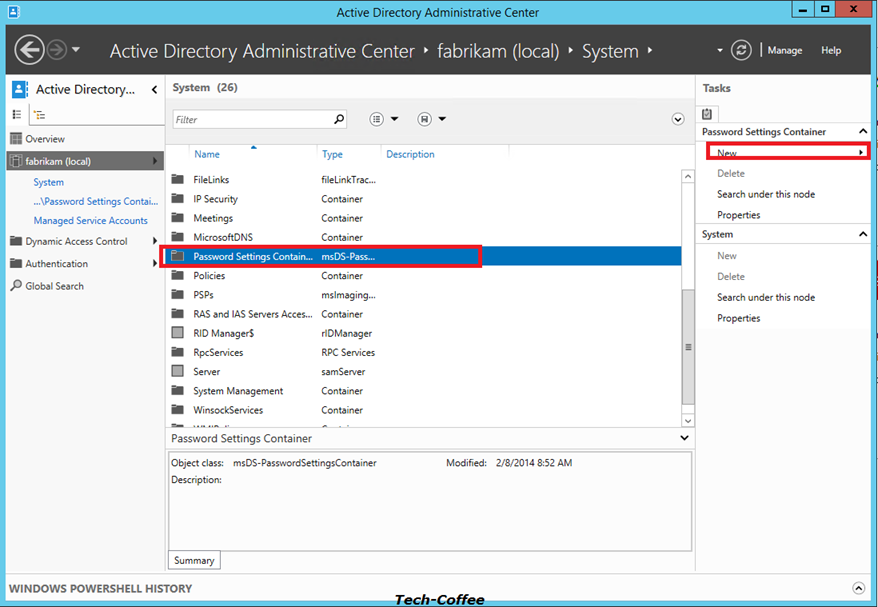
On the PSO creation screen, you can see the password policy parameter such as password length, password history, maximum age, complexity etc. There is also the Precedence parameter. As you can see on below screenshot, I have applied PSO to PSO-Standard Users group. For these examples, I have removed the minimum password age to validate just after account creation my PSO. If I leave this setting to 1 day, I have to wait tomorrow to change password …
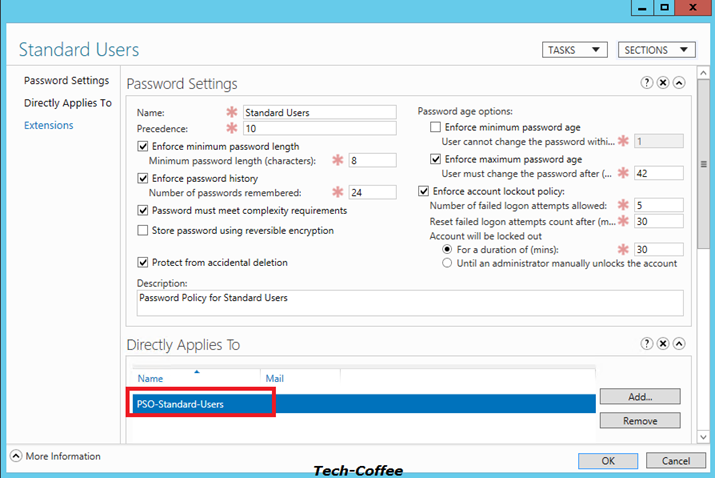
Next I create a stronger password policy that I applied to the PSO-PasswordOfTheDeath group.
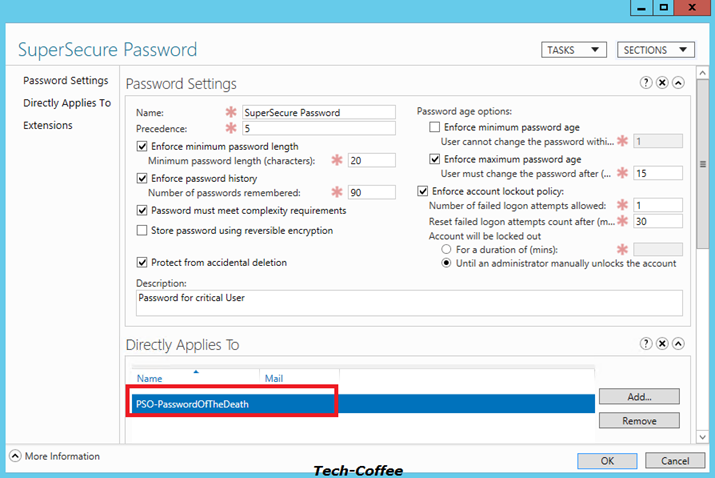
After PSO creation you can double click on the Password Settings Container to view your PSO. On the below screenshot, you can see that my SuperSecure Password PSO has a stronger precedence.
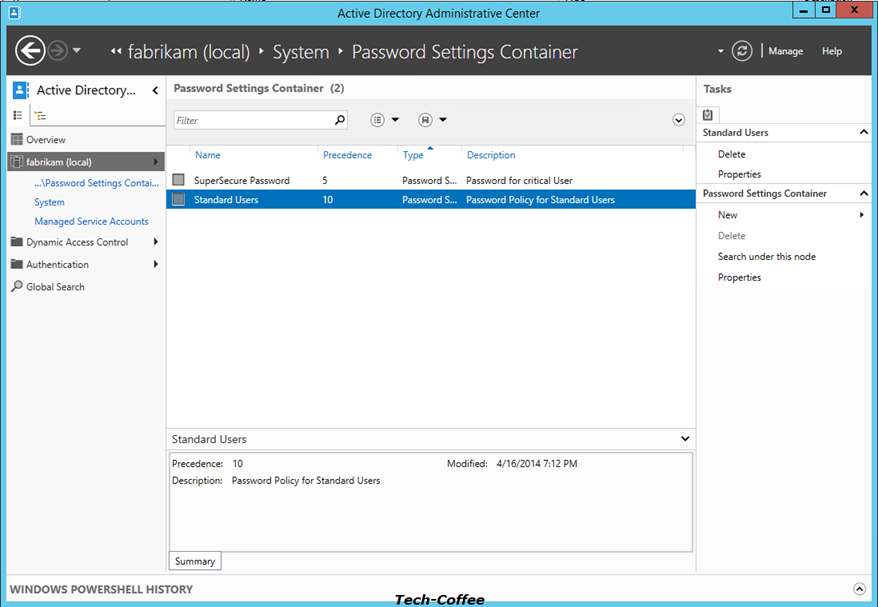
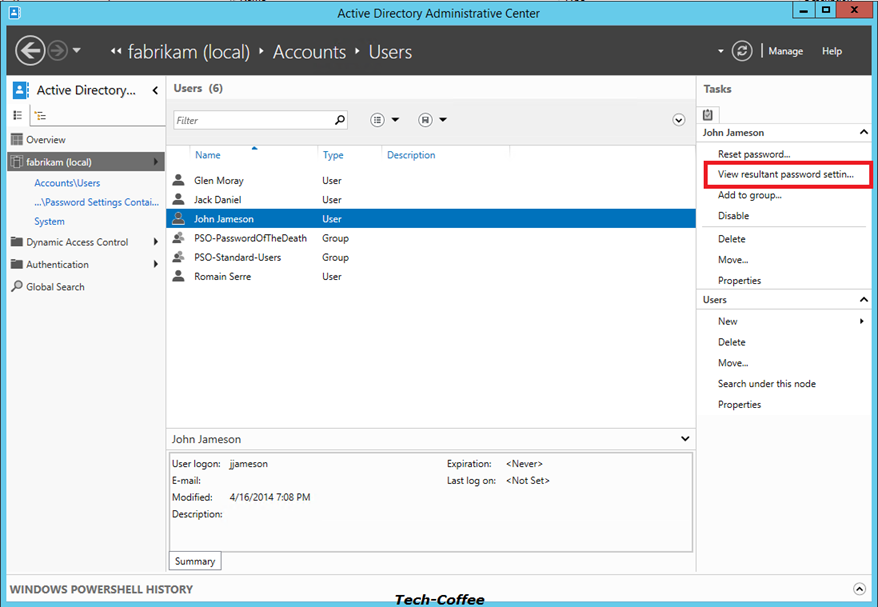
To view the RSOP and so the PSO that will be applied to users, open your OU where are stored your users object and select an account as below. Click on View Resultant Password Settings on right.
Remove default password policy on Active Directory
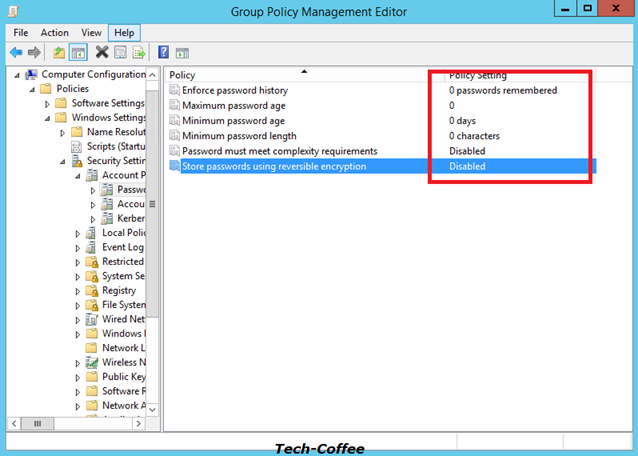
 To validate my test, I remove the default password policy managed by the Default Domain Policy GPO. Open Group Policy management console, and edit the Default Domain Policy.
To validate my test, I remove the default password policy managed by the Default Domain Policy GPO. Open Group Policy management console, and edit the Default Domain Policy.
Open Software Settings, Windows Settings, Security Settings, Account Policies and Password Policies. Set these policies as below.
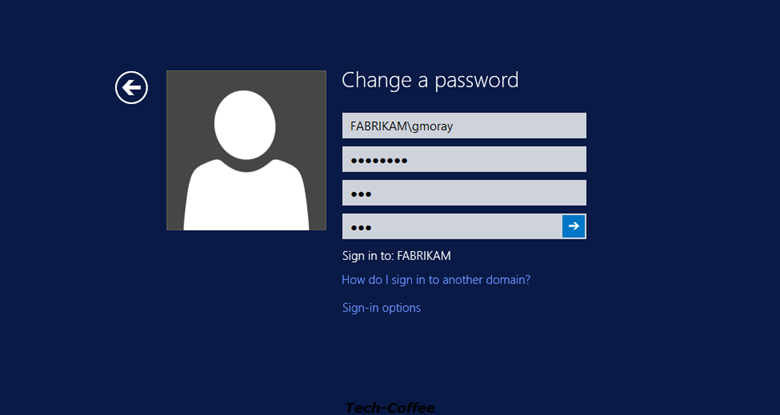
First test: user without password policy
My First user called Glen Moray belong no group. So no password policy is applied to this account. To test that, I change the password to aaa as below:
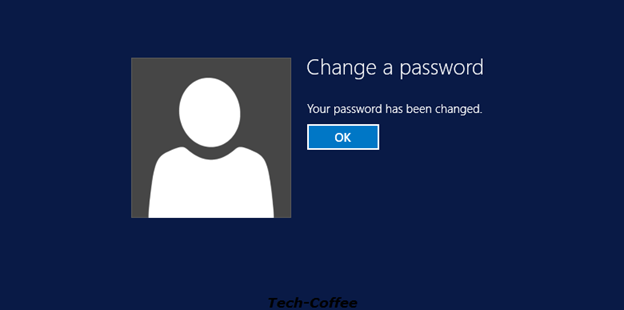
Because no password policy is applied to this account, the password has been changed successfully.
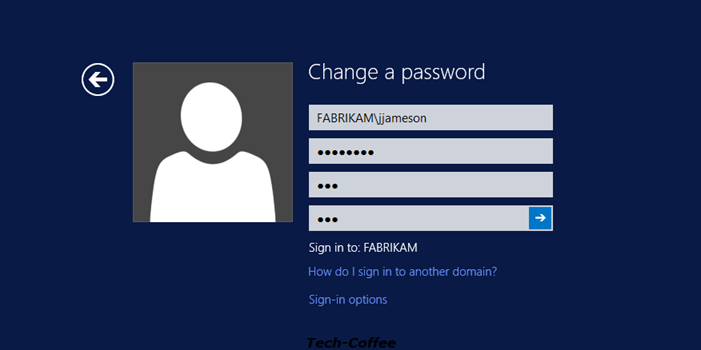
Second test: User with standard users PSO
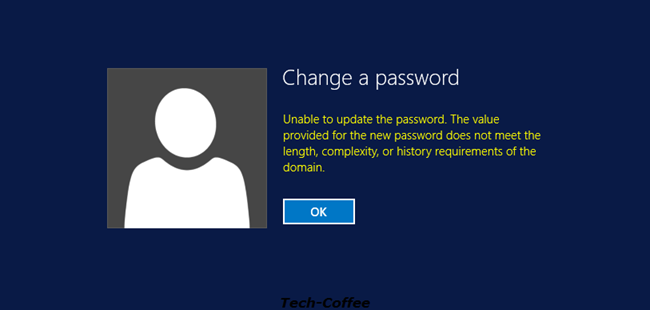
The user John Jameson is linked to the Standard Users PSO. A 8 chars complex password is required. So I try the aaa password:
Because the PSO is applied, the password can’t be applied because it does not meet the requirement related to the PSO.
So I try a complex password more than 8 chars:
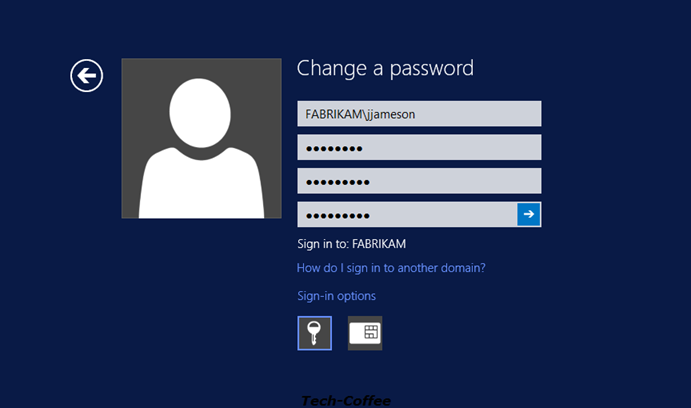
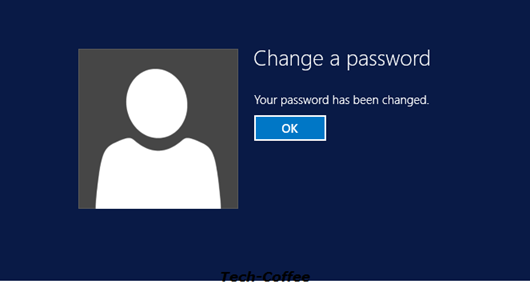
The password meets the PSO requirement so it has been changed successfully.
Third test: User with SuperSecure Password PSO
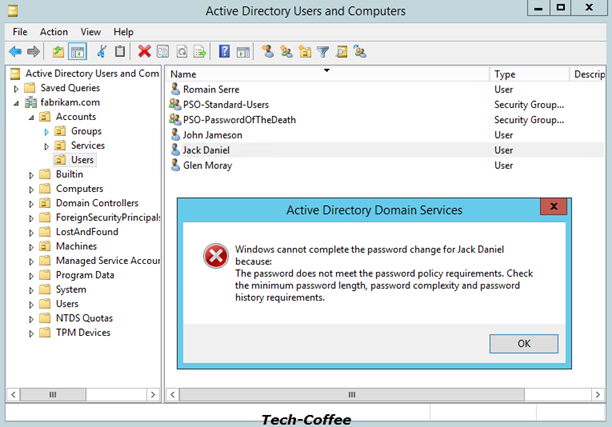
Now I try Jack Daniel user. This user is a member of all my PSO group. But because SuperSecure Password PSO has the strongest precedence, this is this last that will be applied. Let’s try to validate this assumption. I try the same password than John Jameson user:
Because this password doesn’t meet the SuperSecure Password PSO requirement, the password can’t be changed.
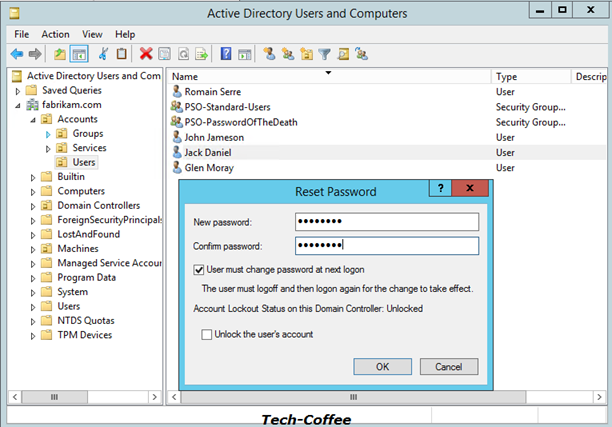
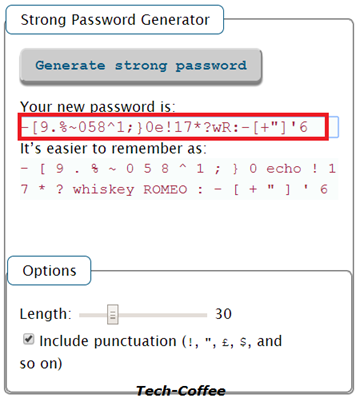
So I generate a strong password with this tool.
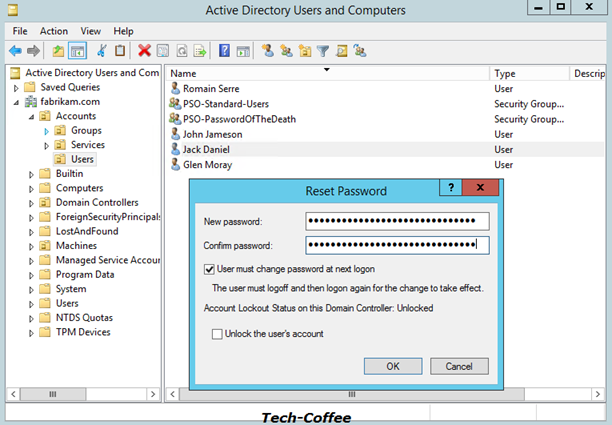
Next I Past it to the reset password wizard:
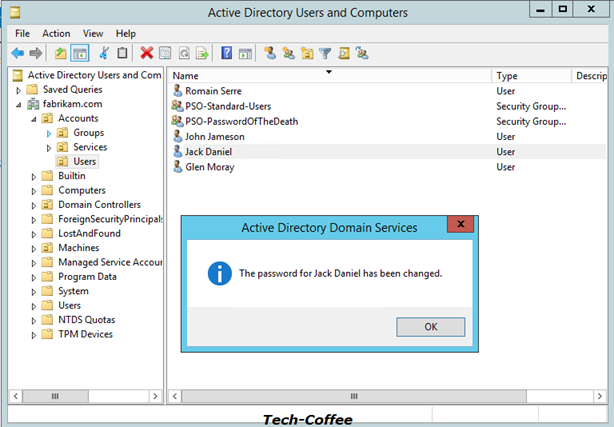
And it is work !
Conclusion
Fine-Grained Password Policy is a great feature that enables to apply different password policies in your domain. For example you can apply a different password policy to administrator, to standard user and to service account. You are no longer forced to use only one password policy. Now that Microsoft has introduced the Active Directory Administrative Console (ADAC), Password Settings Object can be managed easily. So why continue to live without?








great post! How can i configure password settings in 2008? bcoz ADAC tool not available in 2008 right?
Hi,
ADAC is only avaible since Windows Server 2012. For earlier Windows Server version, have you tried something like this:
https://technet.microsoft.com/en-us/library/dd391898(v=ws.10).aspx
Romain
Awesome blog…
Thank you very much Nancy 🙂
Great post, thanks, I really needed this! 🙂
Thank you for the great blog
I have a question regarding modifying the default domain policy , why did you have to change the default values in order for the password setting to be applied ? is this change essential and do we have to do the same if we are applying the fine grained policy to a small number of users ?
Hi,
It is just to show that PSO are not linked to GPO.
I have one doubt – We have to set new password policy for windows 10 machines, If FGPP is applied for the users through Group on windows 10 Organizational unit, does this apply to all the members of the group regardless of the machine they’re on? To put it another way, will this replace the password policy for these users for the whole domain, even if they’re not on a Windows 10 machine?
Yes indeed. If you apply the FGPP to a user, the policy follow the user and FGPP policy has priority against default domain policy.
If I add a password policy, where there was none, will it affect users “immediately” or only the next time they try to change their password. For example, a user has a 6 character password and we implement a minimum of 8 characters. We would like it not to affect users right away, but rather we will tell users to change their passwords, and at that time, follow the new password policy. Thanks
Hey,
The policy will be applied the next time they change password. But you can enforce to ask to change password immediately to all domain users.
A sentence may have an error:
When PSO is applied on some users, there are no longer using password policy from Default Policy Settings GPO. Instead they use the PSO settings.
Do you mean: “…they are no longer using passwored policy from Default Policy Settings GPO”?
Thanks for your information. I am studying network securiy in college.
Yes you’re right. It what I mean
We have a Default Domain Policy that manage password rules. We also create a Fine-Grained Password Policy in Active Directory for a selected group. The policy work fine but if we run a gpresult /r for one of the selected user with the fine grain policy we get the Default Domain Policy Filtering: Denied (Security).
Is this a normal behavior? Also, does all other policy push by the Default Domain Policy should be apply if we add a Fine grain Policy?
Hi! Thank you for this very helpful piece.
However, I found an error in the section “Remove default password policy on Active Directory”.
You write: Open Software Settings, Windows Settings, Security Settings, Account Policies and Password Policies.
But it should be: Open Computer Configuration, Policies, Windows Settings, Security Settings, Account Policies and Password Policies.
The screenshot you added is correct but the text is not.
Thank you, bye!
Good article about Fine grained Password policy. In Detailed explanation with screen shots .Thank you Romain Serre for posting this article
Stuff is Great
You might want to try reading what you have written as the quality of the english is poor.